The 9-Minute Rule for Risk Management Enterprise
Table of ContentsThe 8-Minute Rule for Risk Management EnterpriseIndicators on Risk Management Enterprise You Need To KnowAbout Risk Management Enterprise
Control who can see or modify these aspects by setting certain accessibility rights for individual users, ensuring info safety and security and customized use. Enables customers to customize their user interface by picking and organizing necessary data aspects. Offers an individualized experience by allowing personalization of where and exactly how data elements are presented.It allows access to real-time incorporated information immediately. Risk Management Enterprise. Likewise, this helps get rid of lost time on manual report collection. Also, facilities can use extensive data intelligence for quicker and much more informed decision-making. It enables the automated production of stakeholder reports for individuals or teams. Makes it possible for prompt decision-making and lowers delays created by outdated details.
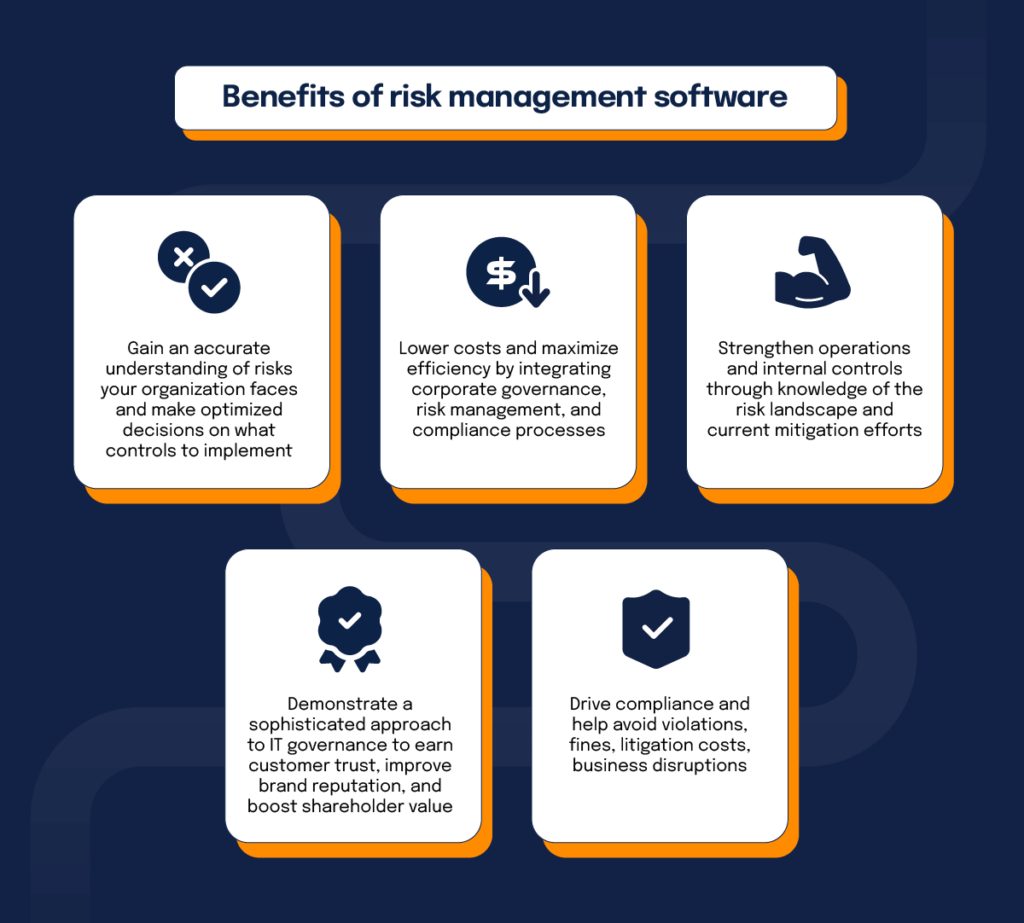

Diligent is a threat administration software program that permits optimizing efficiency, and enhances development. It additionally assists keep track of dangers with ERM software program that consists of incorporated analytics and adapts to your company requirements. This software application features numerous valuable features. Below we have highlighted one of the most essential ones. So, inspect them out.
Some Known Factual Statements About Risk Management Enterprise
It likewise supplies one-click records. In addition, it gives your leadership and board the real-time understandings they require. Simplifies the procedure of accumulating risk data from various components of the company. Risk Management Enterprise. It permits simple modification of records and storyboards. Supplies leadership and the board with real-time danger understandings. Use ACL's sophisticated analytics to spot here threat patterns and predict hazards.
This enables business to record risk understandings and warnings in the third-party vendor's safety and security record. This permits saving risk analyses as auditable documents. It likewise permits exporting them as PDFs. To finish the process firms can complete a review date. Enables companies to record and record risk insights and red flags in third-party vendor protection reports.
Determining threats in development assists a center plan for audits. It additionally minimizes threat through structured conformity and danger monitoring. Due to this centers won't need to manage different systems for threat monitoring. The users of Hyperproof can systematize threat monitoring in one location. It can aid gather and track all your risks in the Hyperproof danger register.
It gives quick accessibility to required details and paperwork. This ensures the safety of Hyper proof instances by making it possible for multi-factor authentication (MFA) using authenticator applications such as Google Authenticator, Microsoft Authenticator, or Authy.
Getting My Risk Management Enterprise To Work
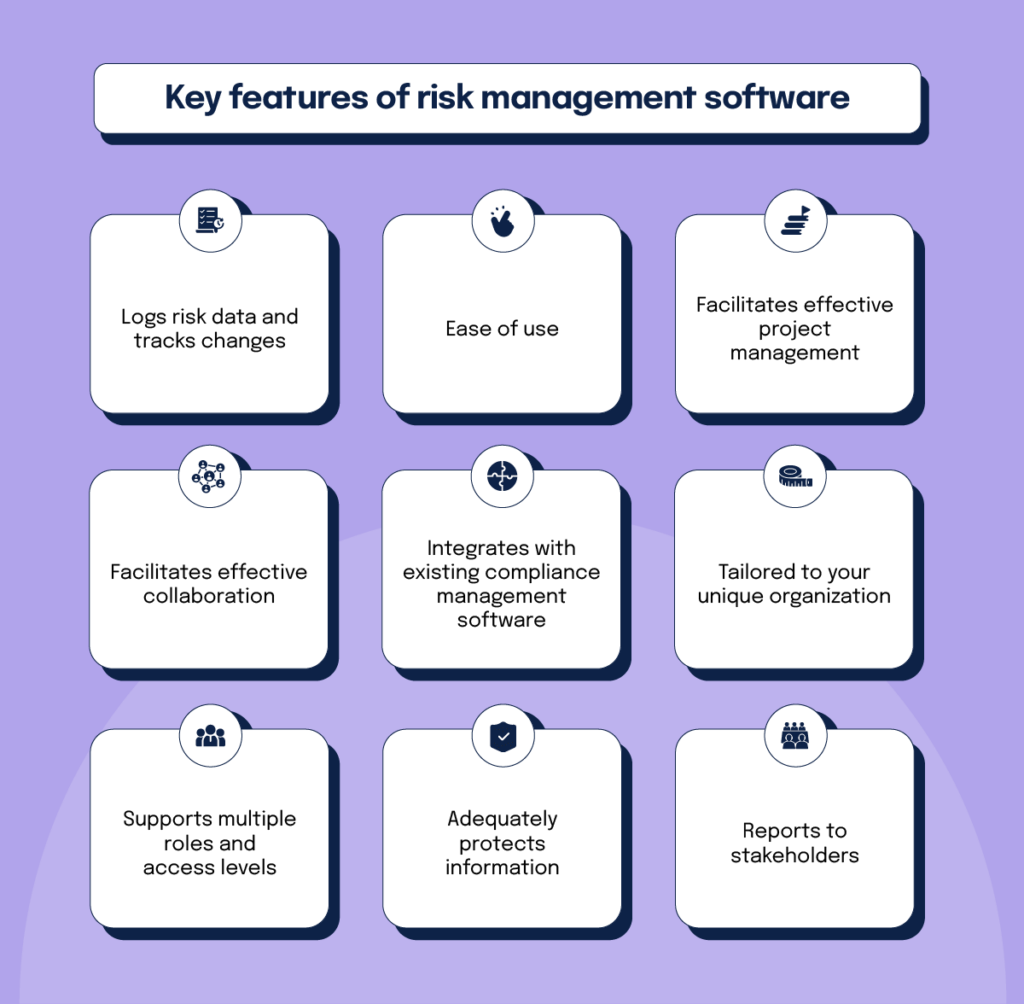
It supplies top-tier protection functions to secure delicate data. This threat monitoring software is an excellent device for facilities looking to fix unnecessary concerns or risks.
Users can likewise utilize the AI-powered tools and pre-existing web content to create, evaluate, prioritize, and address threats efficiently. Improves the process of configuring and populating threat signs up. Makes use of AI and collection content to boost threat evaluation precision. It allows quicker recognition and reduction of dangers, This is mainly an aesthetic version.